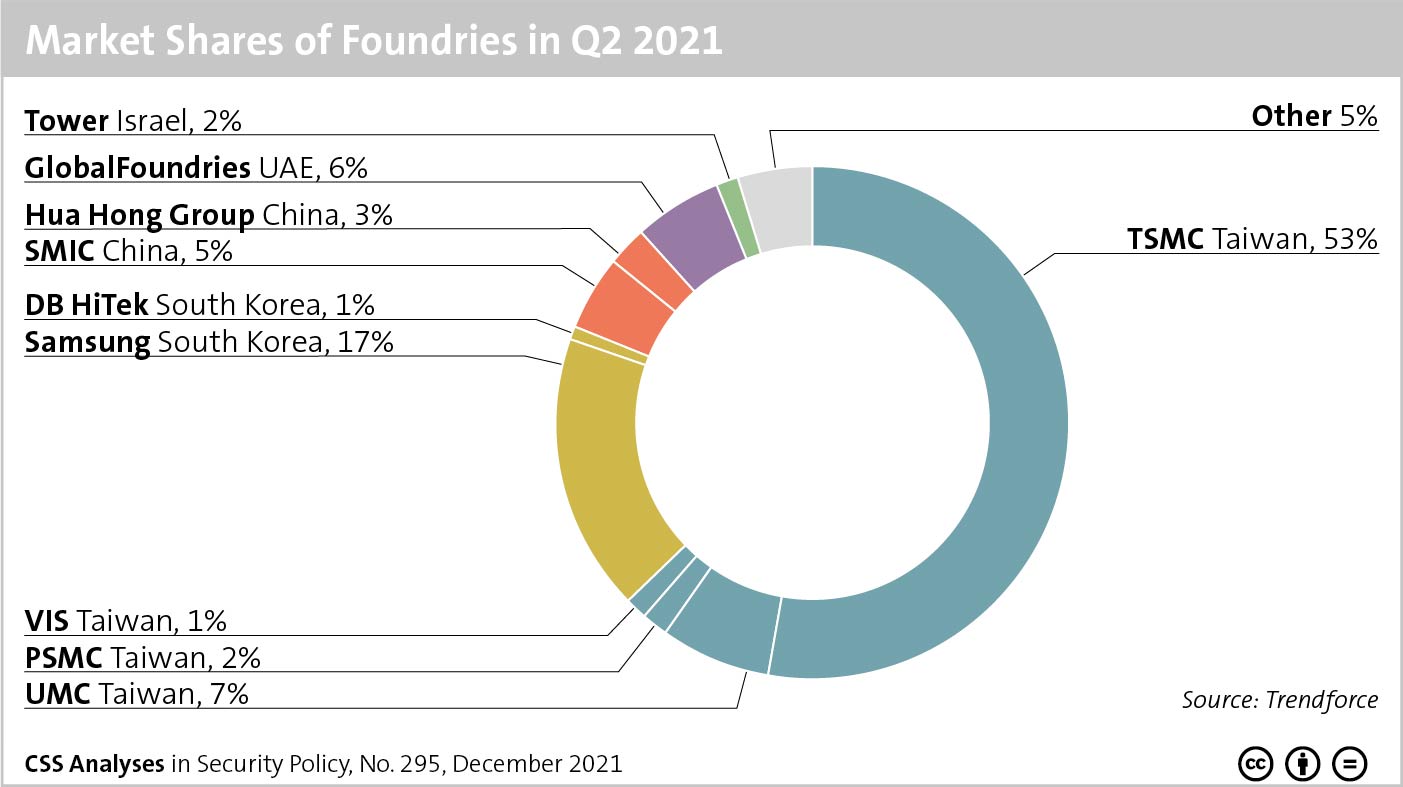
This week’s featured graphic shows market shares of companies in the chip industry, more specifically in its contract manufacturing segment. For more information on microchips and on fragile networks underpinning the semiconductor industry, read Julian Kamasa’s CSS Analysis in Security Policy here.