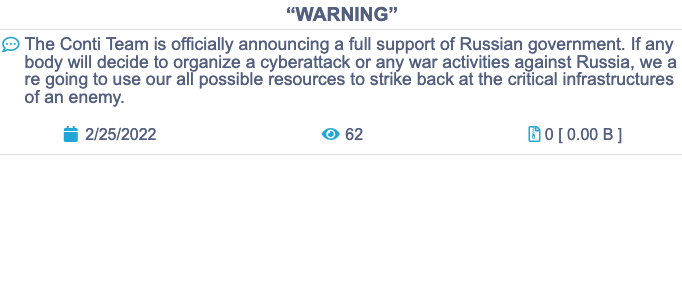
A day after Russia’s President Putin ordered the full-scale invasion of Ukraine, Conti, a hacker group suspected to be largely based in Russia and known for financially extorting Western companies, published a message in support of Moscow. The hackers threatened to use “all possible resources to strike back at the critical infrastructures” in retaliation for any “cyberattack or any war activities against Russia”. Soon after, the group sought to dial back this message, claiming not to side with any government.

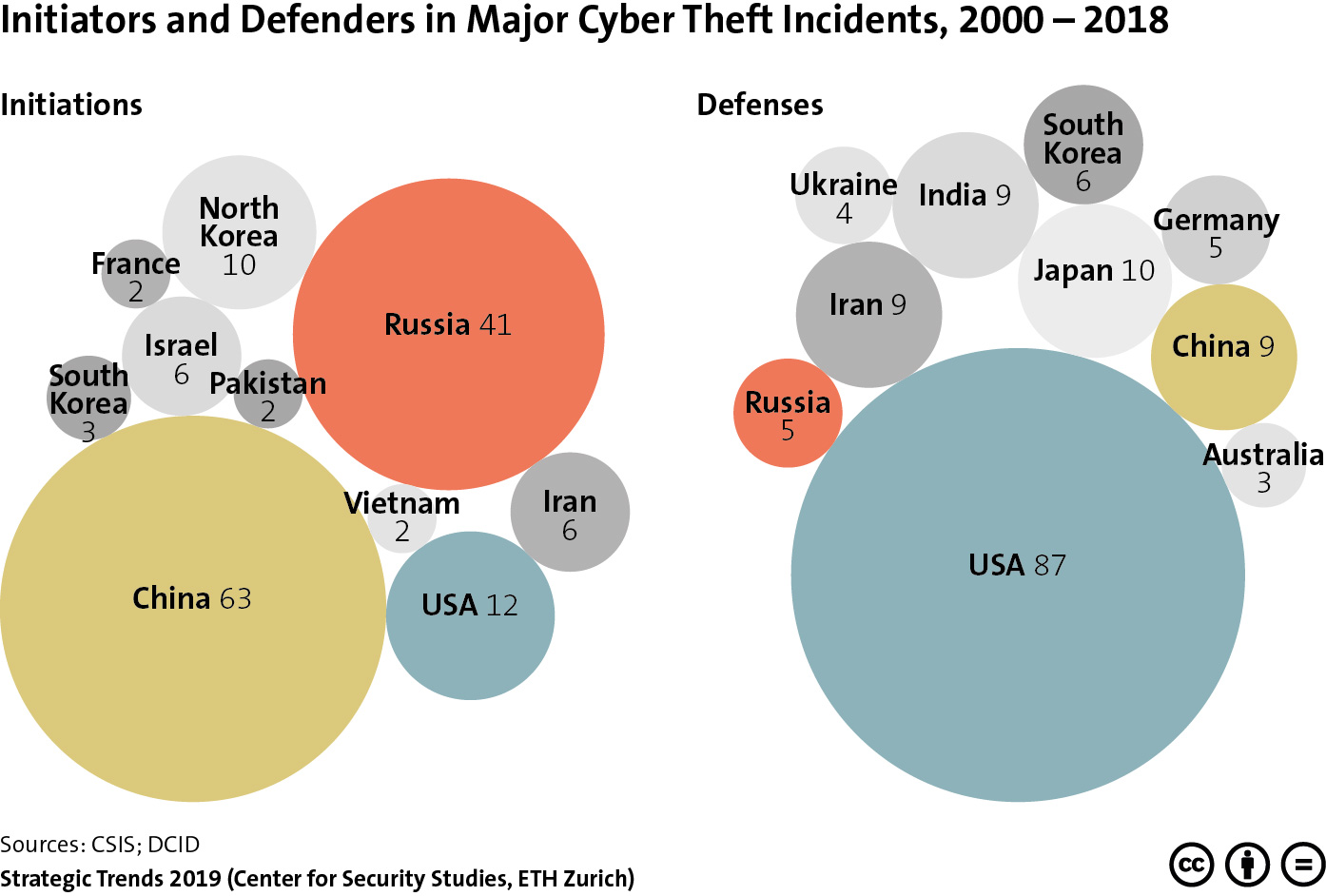
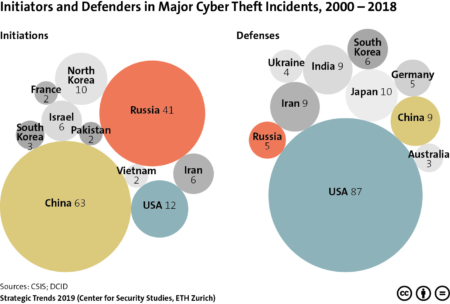
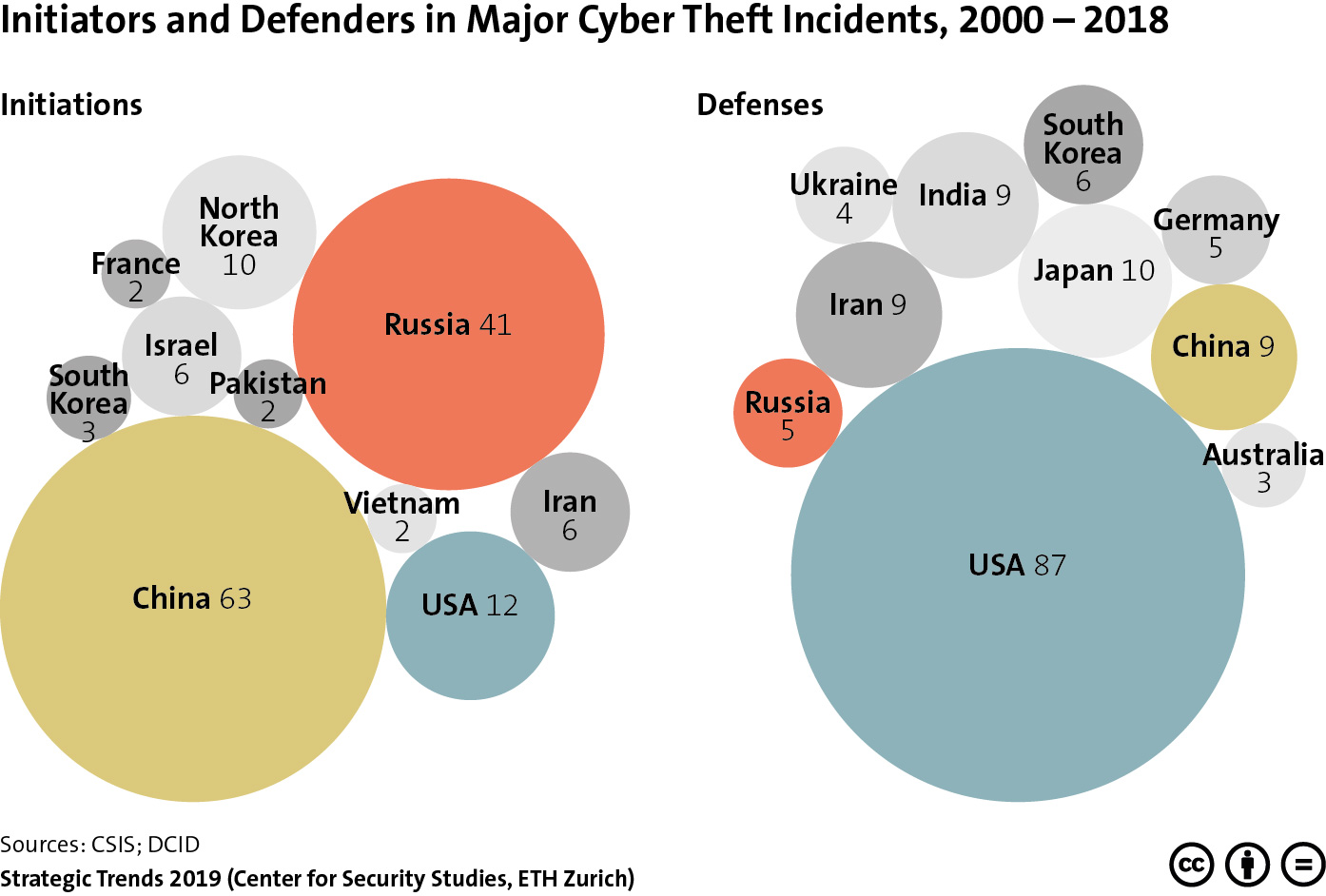 This graphic provides an overview of the nations in which major cyber theft incidents were initiated, as well as the countries affected by these attacks between 2000 and 2018. To find out what this highlights about the eclipse of Western military-technological superiority, read Michael Haas’ chapter for Strategic Trends 2019
This graphic provides an overview of the nations in which major cyber theft incidents were initiated, as well as the countries affected by these attacks between 2000 and 2018. To find out what this highlights about the eclipse of Western military-technological superiority, read Michael Haas’ chapter for Strategic Trends 2019