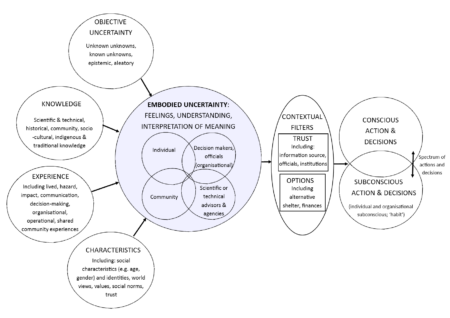
Image: The Concept of Embodied Uncertainty as visualized by Sword-Daniels et al. (2018)
Affluence and vulnerability are often seen as opposite sides of a coin – with affluence generally understood as reducing forms of vulnerability through increased resilience and adaptive capacity. However, during the past ten years, my research with a range of colleagues has consistently highlighted the need to re-examine this dynamic relationship in the context of climate change, natural hazards, and associated disasters. A new collaboration recently provided an opportunity to develop this work further, by applying resilience thinking from the realm of disaster research to another pressing research topic: cyber security.

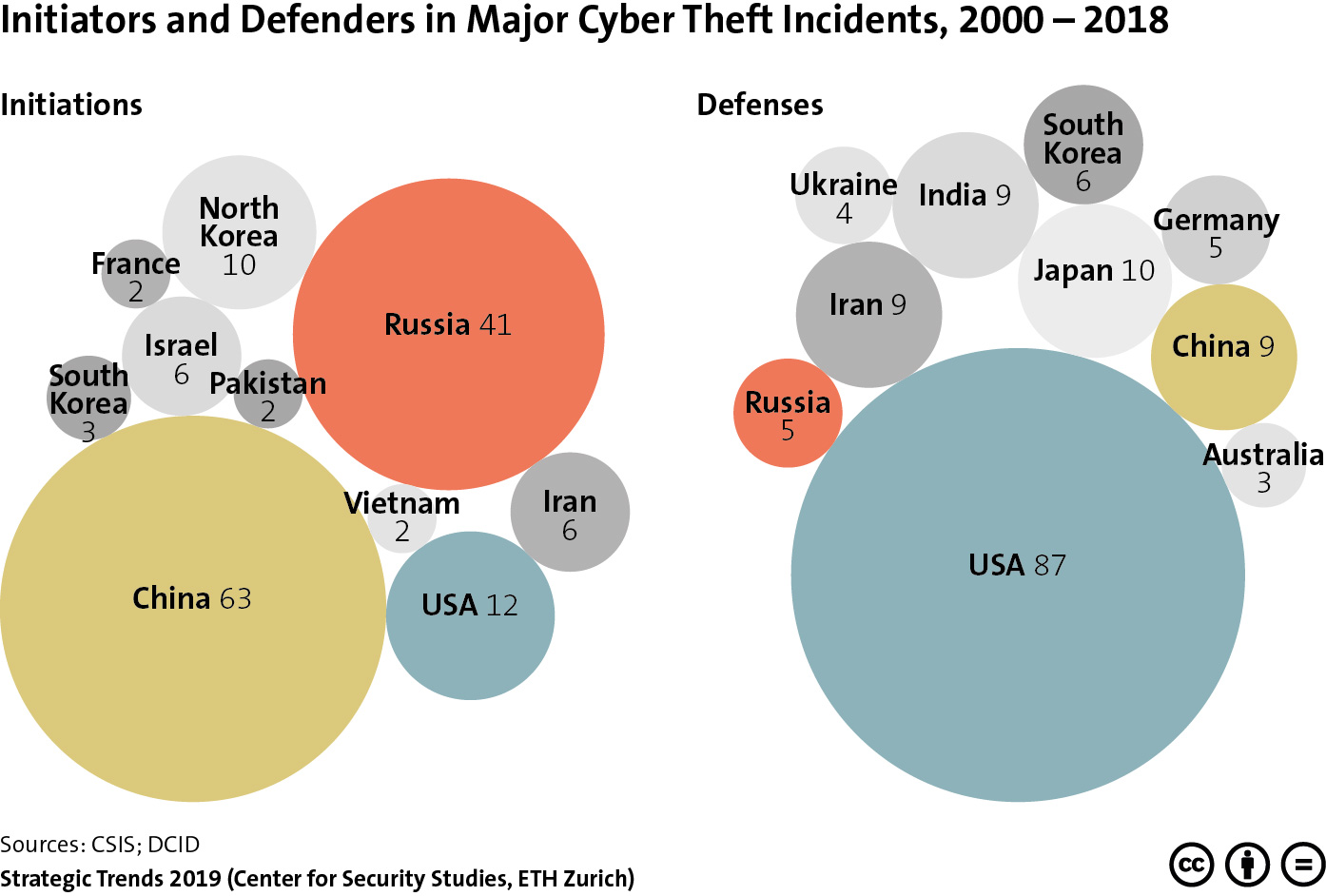
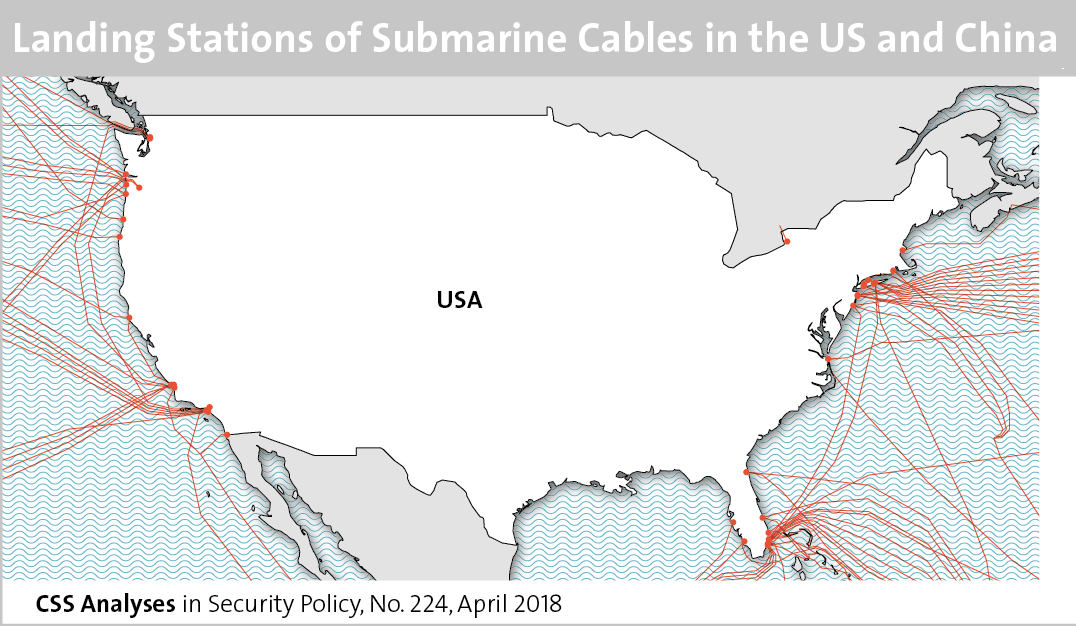
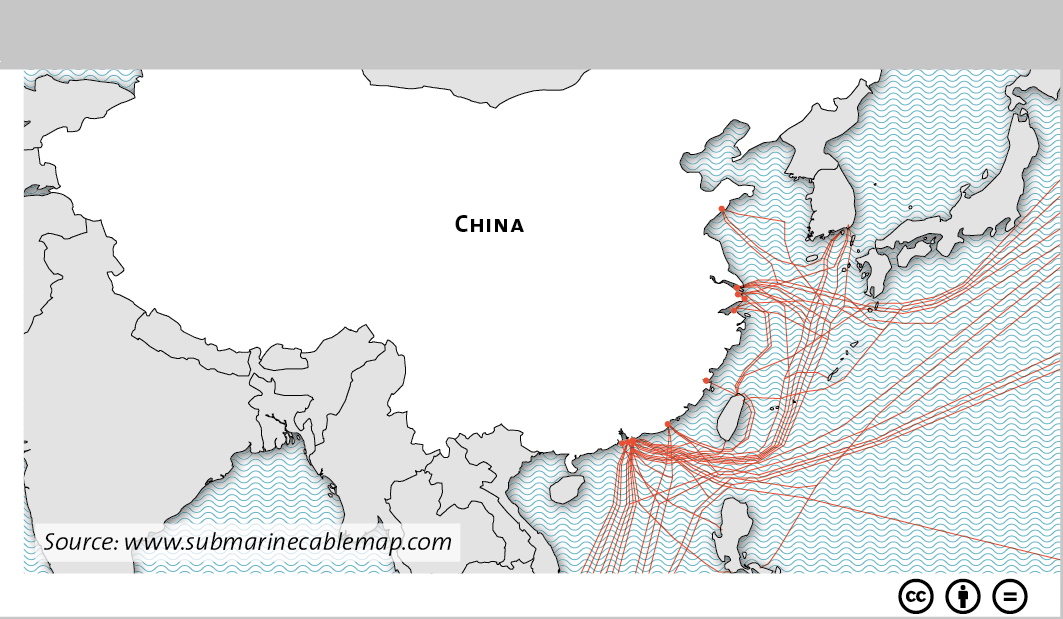 This graphic maps the various landing stations of submarine cables in both the US and China. To find out about cybersecurity in Sino-American relations, see Marie Baezner’s CSS’ Analyses in Security Policy series
This graphic maps the various landing stations of submarine cables in both the US and China. To find out about cybersecurity in Sino-American relations, see Marie Baezner’s CSS’ Analyses in Security Policy series