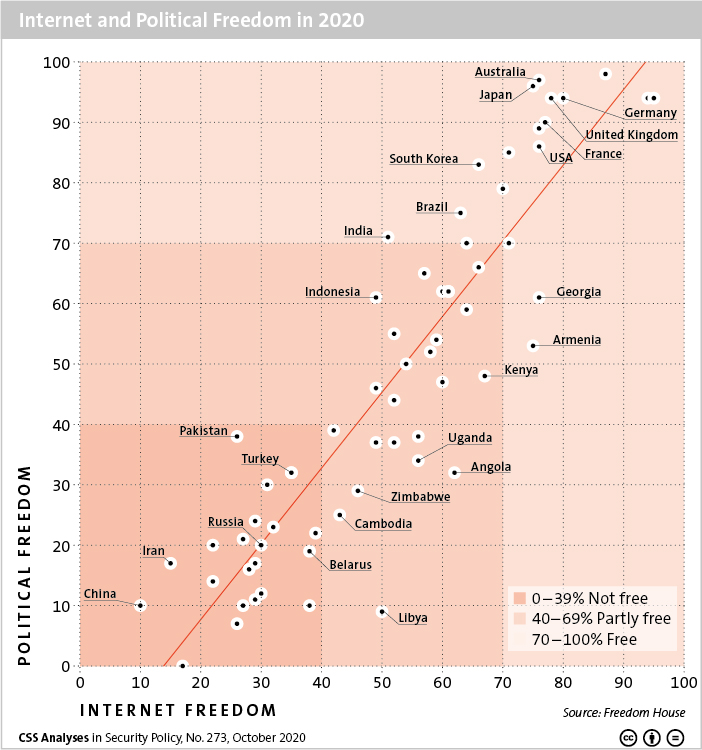
This week’s featured graphic compares the results of two Freedom House reports on political freedom and Internet freedom, which suggest there’s a link between the two.
For more on how Internet freedom is in retreat, read Julian Kamasa’s CSS Analysis in Security Policy here.

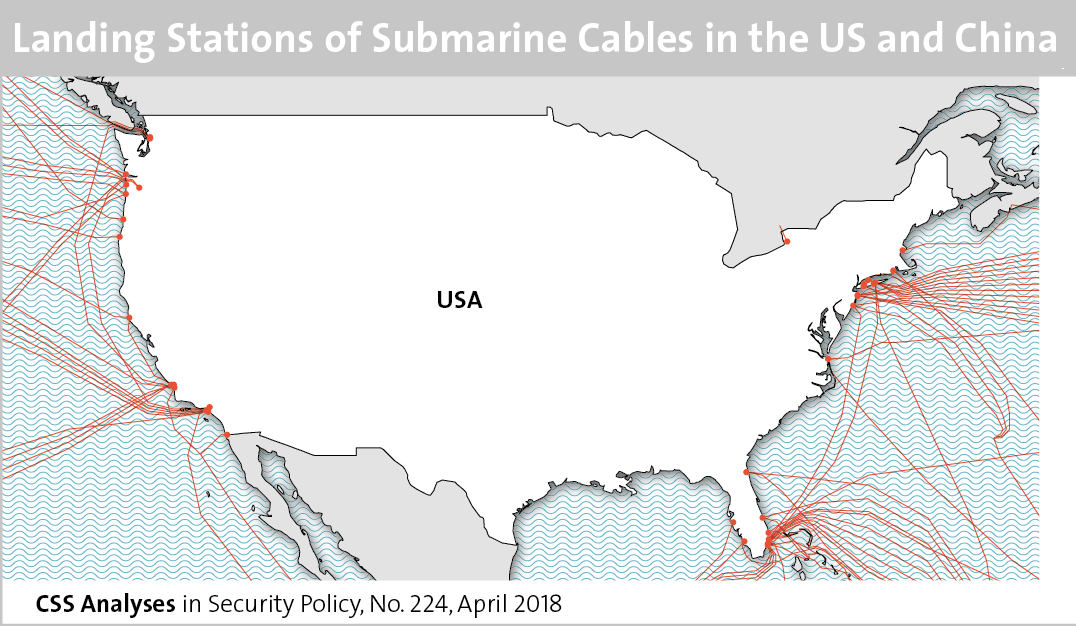
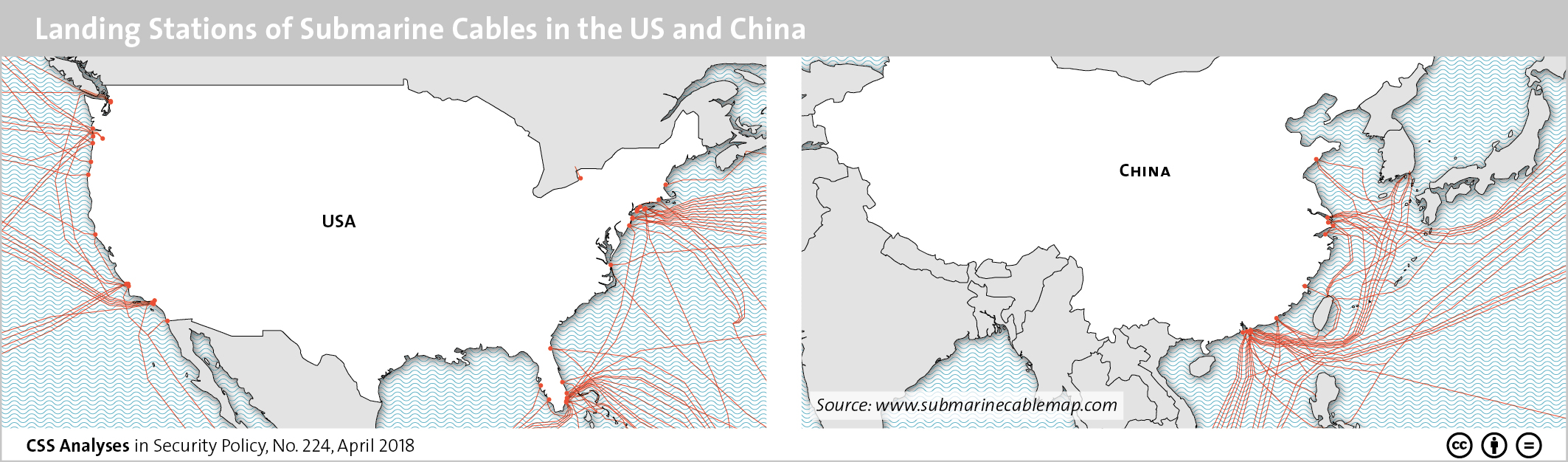
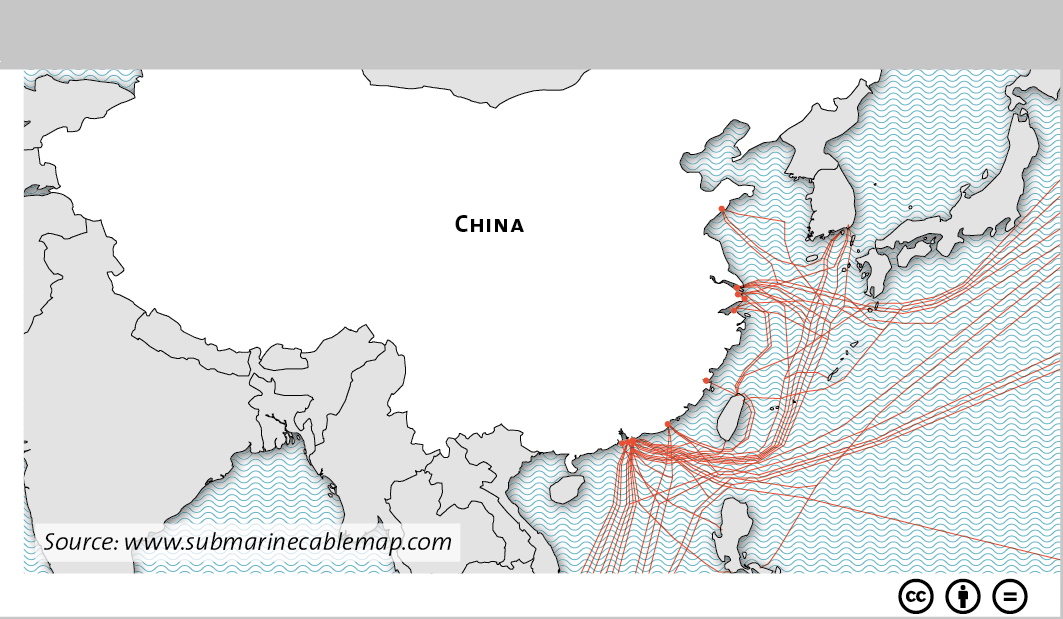 This graphic maps the various landing stations of submarine cables in both the US and China. To find out about cybersecurity in Sino-American relations, see Marie Baezner’s CSS’ Analyses in Security Policy series
This graphic maps the various landing stations of submarine cables in both the US and China. To find out about cybersecurity in Sino-American relations, see Marie Baezner’s CSS’ Analyses in Security Policy series