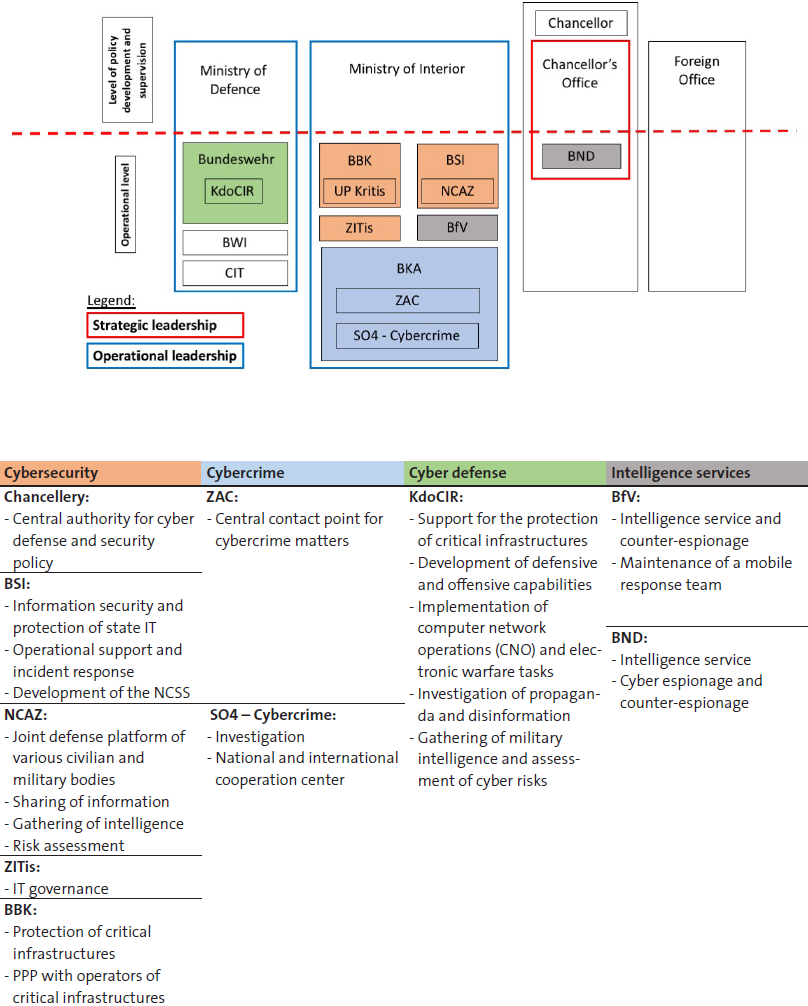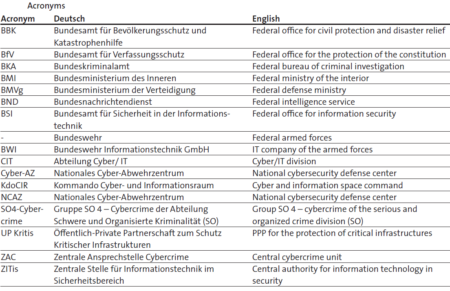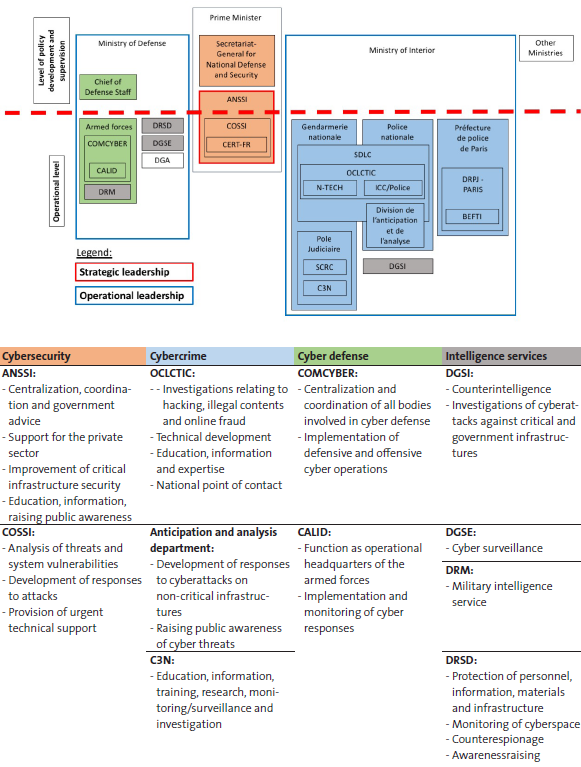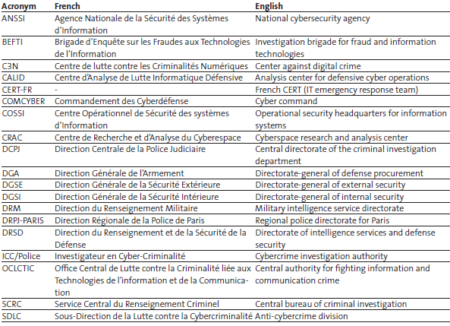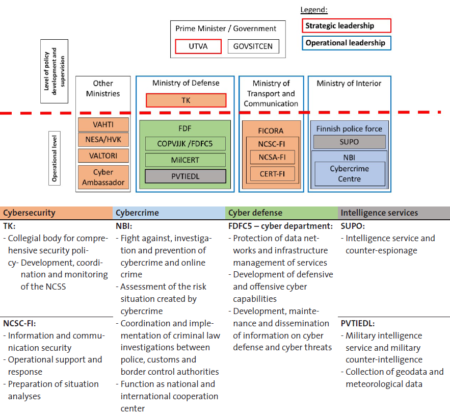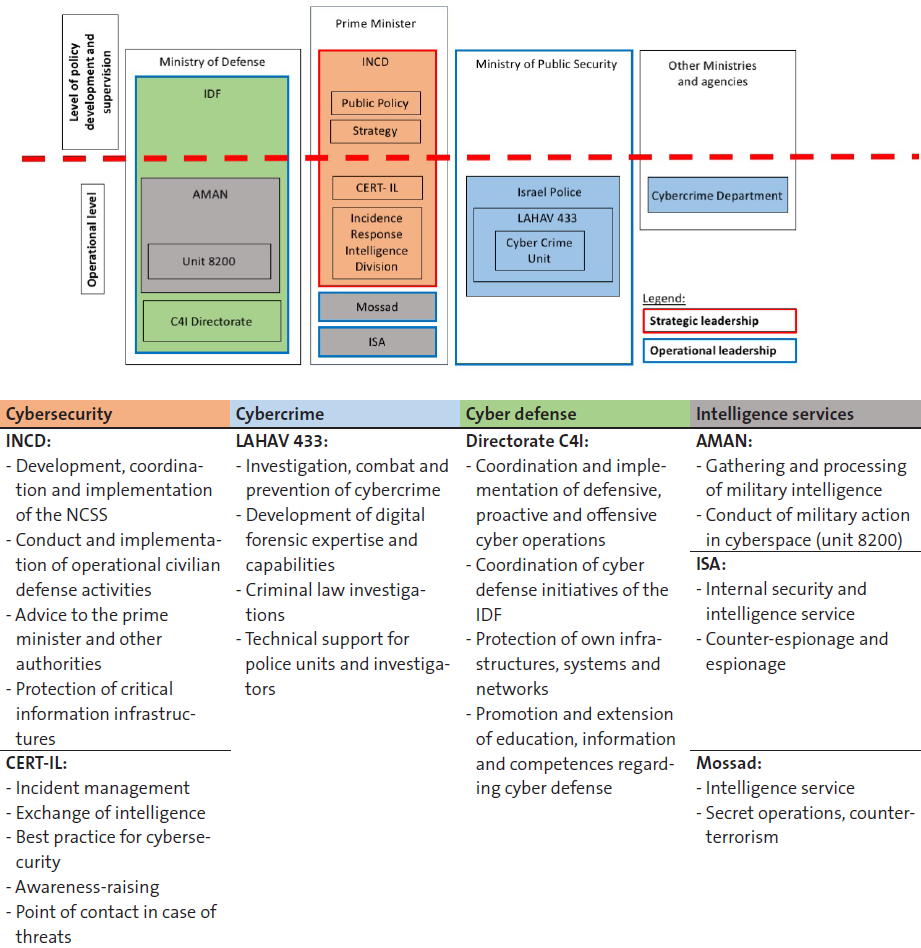
This week’s featured graphics outline how cybersecurity responsibilities are shared among governmental organizations in Israel. For more information on national cybersecurity strategies and cybersecurity challenges in Israel, as well as in Finland, France, Germany, Italy, the Netherlands and Switzerland, read Marie Baezner and Sean Cordey’s CSS cyber defense report here.