This article (PacNet #36) was originally published by the Pacific Forum CSIS on 22 June 2015. It draws upon a recent CIGI Graduate Fellows Policy Brief, which is available here.
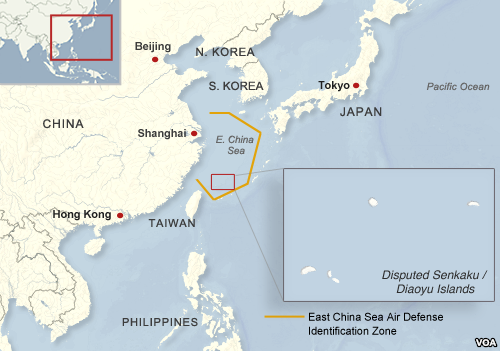
In November 2013, much to the surprise and alarm of the international community, China announced the creation of its “first” Air Defense Identification Zone (ADIZ) in the East China Sea. There is growing concern that China will implement a second in the South China Sea, an unstable area riddled with maritime and territorial disputes. The November announcement prompted journalists, policy makers, and scholars to understand and explain the political and security implications of China’s ADIZ. A common concern was that China appeared to be using its ADIZ as a means of asserting sovereignty over the disputed Senkaku/Diaoyu Islands. Much of the subsequent analysis and commentary misrepresented the actual global state of play with respect to ADIZs, as well as their purposes and functions. The result was a great deal of unnecessary criticism and tension. A better understanding of ADIZs is required to prevent similar disputes in the future. But even better than an improved understanding would be a uniform global regime with consistent and transparent practices so that aviation safety and maritime or territorial disputes do not compromise each other in the future.
Background
An ADIZ is defined in the 1944 Chicago Convention of International Civil Aviation as “a special designated airspace of defined dimensions within which aircraft are required to comply with special identification and/or reporting procedures additional to those related to the provision of air traffic service.” Originally implemented in the postwar/Cold War period, ADIZs functioned to facilitate the early identification of inbound aircraft and reduce the frequency and inherent risks of airborne interceptions. ADIZs were not a matter of international concern until China’s 2013 announcement of an East China Sea ADIZ.
Despite the Chicago Convention’s tacit authorization of ADIZs, there is no international regulation or guidance for implementing or operating them. They are neither explicitly prohibited nor permitted under international law. As a result, practices are inconsistent which has led to misunderstandings that have the potential to inflame international tensions.
Current Context
Currently, much of the research and information available on ADIZs is outdated or incorrect. There are common misconceptions about the number of countries currently operating ADIZs, the specific procedures of each country’s ADIZ, as well as their legal and political implications.
Information on an ADIZ may be found in the operating country’s Aeronautical Information Publication (AIP). However, much of this information is difficult to access. The closest thing to a single repository is the Jeppesen Pilot Manuals, which provide comprehensive aeronautical navigation data. From these it is possible to identify the 16 countries that currently operate ADIZs.
China’s East China Sea ADIZ overlaps with those of Japan, Taiwan, and South Korea and includes airspace over the disputed Senkaku/Diaoyu Islands. For this reason, Japan interpreted China’s move as an assertion of sovereignty and a step in a larger plan to incrementally assert control over the East China Sea.
Not only was China criticized for attempting to use its ADIZ as a tool for asserting sovereignty (something no ADIZ can accomplish under international law), it was also hotly criticized for demanding that even aircraft engaged in innocent transit of its ADIZ without entering sovereign Chinese airspace give advance notice of their intentions and identify themselves to Chinese authorities. In fact, several other countries enforce this requirement, including the United States. However, the specific requirements and procedures China sought to impose were vague resulting in confusion and justified concern.
The recent politicization of ADIZs is worrying for two reasons. First, it threatens to undermine their utility as confidence-building mechanisms. While originally conceived and framed as tools for national security, ADIZs have in fact proven capable of enhancing regional security by promoting aviation safety, enhancing transparency, and reducing uncertainty. The politicization of ADIZs threatens to increase, rather than decrease, the dangers of inadvertent conflict in the skies.
Second, framing ADIZs as tools for sovereignty assertion can only increase political tensions in contested areas. Of particular concern here is the South China Sea, which would be a logical next step for Beijing, not only because of its expansive and contested maritime and territorial claims, but also because China has many sensitive military installations in the area.
A uniform global regime on ADIZs specifying best practices would help depoliticize them and reduce the dangers associated with passive noncompliance, deliberate challenges, unnecessary or overly frequent scrambles, simultaneous interceptions, collisions, and outright hostile actions – dangers well illustrated by recent surprise encounters between Russian and North American Treaty Organization aircraft, the dramatic spike in Japanese scrambles and, most dramatically, the 1983 shooting down of Korean Airlines Flight 007 and the 2001 Hainan Island EP-3 incident.
Recommendations
In light of widespread misinformation and confusion regarding the status and operation of ADIZs, we recommend the following steps that would help depoliticize ADIZs, increase transparency, build confidence, reduce the risk of inadvertent crisis, and ultimately promote trust.
The ICAO should establish a template for ADIZ best practices. This template should clearly specify the purposes of an ADIZ:
- allowing for the timely identification of aircraft to reduce the risk of surprise attack;
- promoting regional security by routinizing and making transparent air defense identification and interception procedures;
- reducing the frequency of unnecessary scrambles (thereby reducing costs, wear-and-tear, and crew fatigue of the kind that erodes tactical situational judgment);
- reducing uncertainty; enhancing transparency; and building confidence.
- The template should also clarify that an ADIZ does not have maritime or territorial sovereignty implications. It should suggest (minimally) or mandate (maximally) procedures for managing ADIZ overlaps, perhaps using the current India- Pakistan agreement as a model.
The ICAO should create a single, publicly accessible repository for all ADIZ-related information to promote transparency. This information should be accessible at no cost and should include reporting and updating requirements.
The international community should engage in quiet, informal dialogue about how to effectively manage and administer ADIZs, especially in East Asia, where zones overlap. These talks should center on depoliticizing the current understanding of ADIZs and rebuilding confidence between countries in the region. Conversations may also lead to more formal agreements in the future.
Conclusion
When properly understood, ADIZs can, serve as public goods promoting aviation safety and regional security, but if politicized and treated as tools or chessboards for sovereignty assertion, they jeopardize, rather than promote, regional and national security.
Under good regulation, and when seen in a nonpolitical light, ADIZs are more to be welcomed than feared.
PacNet commentaries and responses represent the views of the respective authors. Alternative viewpoints are always welcomed.
Joëlle Charbonneau, Katie Heelis, and Jinelle Piereder are Graduate Fellows at the Centre for International Governance Innovation. Joëlle Charbonneau and Jinelle Piereder are also M.A. candidates in Global Governance, and Katie Heelis is a Master’s candidate in International Public Policy, at the Balsillie School of International Affairs.
For more information on issues and events that shape our world, please visit ISN Security Watch or browse our resources.

